ECS Container Logs to Slack via AWS Lambda
This was more of a discovery article to document the process for getting logs from ECS containers into a messaging service (Slack in this case). I used data from this website’s logs, specifically when the contact form receives spam data and when people go to suspicious paths that don’t exist (primarily automated scanners looking for the WordPress login page or phpMyAdmin…). The below topics are covered:
- Configuring containers running in AWS ECS to send logs to AWS CloudWatch
- Setting the AWS CloudWatch Log Group to Stream the data to an AWS Lambda function
- The Lambda function code for sending the data as Slack messages
Configuring ECS Containers to Send Logs to CloudWatch
I’m assuming if your reading this you have familiarity with AWS ECS and so I’ll jump straight to the good bit.
From the ECS task definition, create a new revision. Select the relevant container definition for which you want the logs.
Scroll down to the Storage and Logging section and configure the Logging details. See the below example.
Setup Slack Incoming Webhook
To receive messages in Slack, a new app needs to be added to the workspace and an incoming webhook generated.
Navigate to https://api.slack.com/apps, select Create New App.
Enter an App Name and select a Development Slack Workspace. Click Create App.
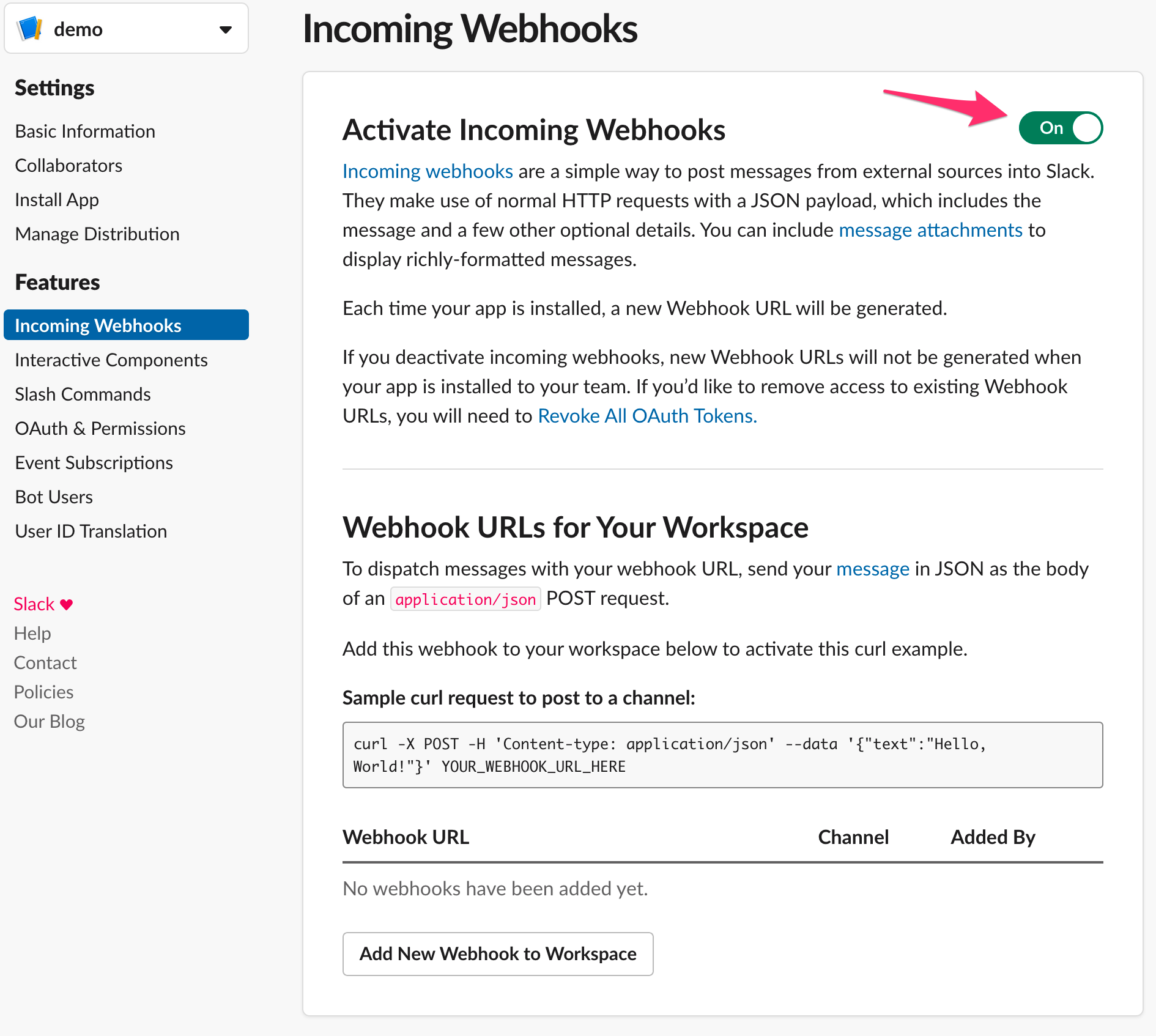
From the basic information page, click Incoming Webhooks.
Activate the incoming webhook. Click Add New Webhook to Workspace.
Select the channel to add the webhook in. Click Install.
Copy the webhook URL for use later.
Create a Lambda Function to Send Messages to a Slack Incoming Webhook
In my case, I used the AWS Toolkit for Visual Studio Code to create the Lambda function. I won’t go into the details of how to use the extension here; however, at a high level, the extension is using Cloudformation to configure Lambda. The only significant change I made to the default template was to remove the API Gateway specifics (since I’m not using them here).
The app.py code I used to send messages to Slack is shown below.
At a high level:
- event_decoder() is used to decode the incoming event data from CloudWatch.
- send_notification() is used to send the actual slack message.
- In main, event_decoder() is called, then using the return checked for some arbitrary message text, in this case, “Bad” which is part of the text when a bad contact form entry is made and “HTTP/1.1” 418" which occurs every time someone hits a suspicious URL like wp-login.php. See the references for more on 418.
Using the Visual Studio Extension, publish the Lambda function to the AWS account. This will require selecting a deployment S3 bucket, a region, and a function name.
|
|
Be sure to check the GitHub repository for an updated version.
Once the Lambda function has successfully deployed, navigate to the settings and define an environment variable SLACK_WEBHOOK. Paste in the incoming webhook URL saved earlier as the value and save the changes.
Configure the AWS CloudWatch Log Group to Stream to AWS Lambda
Navigate to CloudWatch from the AWS Console, click Logs from the left-hand navigation.
Select the ECS log group, click Actions, click Stream to AWS Lambda.
Select the Lambda function created earlier. Click next.
Select the AWS Lambda log format, click next.
Click Start Streaming.
At this point logs coming from the ECS container/s matching the patterns from the Lambda function code will trigger a Slack message to be sent to the configured channel.
References
- Slack - Attaching content and links to messages
- RFC2432 - Section 2.3.2 418 I’m a teapot
- Mozilla - 418 I’m a teapot